eSeGeCe
software
eSeGeCe
software
OpenSSL Perfect Forward Secrecy
From sgcWebSockets 4.4.8 there are small modifications in library to improve security of connections. One of them is Perfect Forward Secrecy
When you use the RSA key exchange mechanism, it creates a link between the server's key pair and the session key created for each unique secure session. Thus, if an attacker is ever able to get hold of the server's private key, they can decrypt your SSL session and any saved SSL sessions.
In contrast, when you enable Perfect Forward Secrecy (PFS), there is no link between your server's private key and each session key. If an attacker ever gets access to your server's private key, the attacker cannot use the private key to decrypt any of your archived sessions, which is why it is called "Perfect Forward Secrecy".
Enable Perfect Forward Secrecy
To enable Perfect Forward Secrecy, for TLS 1.2 connections, just enable the property:
SSLOptions.OpenSSL_Options.ECDHE := True;
This will enable ECDHE for TLS 1.2 connections if you are using openSSL 1.0.2 libraries (for 1.1.1 ECDHE is enabled by default). When ECDHE is enabled, the library pass to openSSL library a list of cipher with high security.
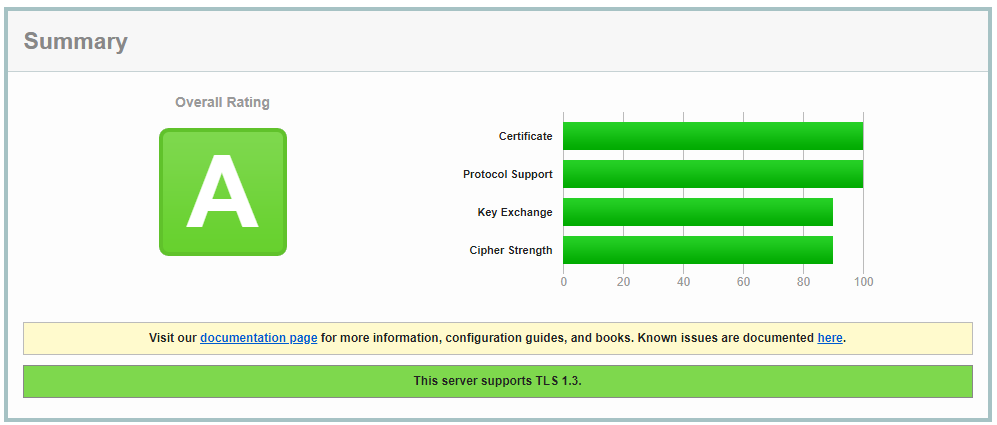
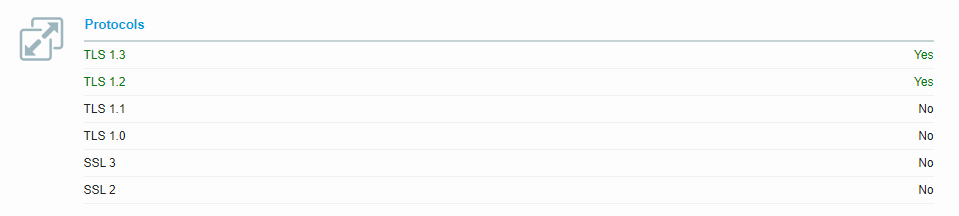
If you do a Security Test in the online web https://entrust.ssllabs.com/, you will get a secure result after enabling ECDHE on your server.
The server used to pass the tests was using openSSL 1.1.1 and allows TLS 1.2 and TLS 1.3, ECDHE was enabled too.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.