eSeGeCe
software
eSeGeCe
software
WebAuthn Server
From sgcWebSockets 2025.4.0 Enterprise, the WebAuthn Protocol is supported (currently in BETA).
WebAuthn (Web Authentication) is a web standard developed by the World Wide Web Consortium (W3C) and FIDO Alliance to enable secure, passwordless authentication on the web. It is part of the broader FIDO2 framework and aims to reduce reliance on traditional passwords, which are often vulnerable to phishing, credential stuffing, and other attacks.
At its core, WebAuthn allows users to authenticate using public-key cryptography. Instead of a username and password, users register a unique public-private key pair with a web application (the Relying Party). The private key is securely stored on an authenticator—such as a hardware security key, smartphone, or built-in biometric device—while the public key is stored on the server.
During authentication, the server issues a challenge that must be signed by the user's private key. The signed challenge is returned and verified using the stored public key, ensuring both the integrity and origin of the response. This approach prevents credentials from being intercepted or reused.
WebAuthn supports a range of authenticators and devices, making it flexible for both developers and users. It also enables multi-factor authentication (MFA) when combined with other factors like PINs or biometrics, significantly improving security without sacrificing usability.
Attestation Formats Supported
Different attestation formats define how this data is structured and verified. Three commonly used formats are android-key, packed, and others like fido-u2f, apple, or none. By default all attestation formats are enabled, you can find below the list of supported attestation formats:
- NoneAttestation: in this case none attestation data is returned. Prioritizes user privacy by avoiding the exposure of device identifiers. Common in applications that don't care about device provenance.
- PackedAttestation: is a flexible, compact format used by many authenticators. The authenticator returns an attestation certificate and signature. Can be: Full attestation: Signed with a vendor-provided key and cert or Self attestation: Signed using the credential private key. Most widely used across different platforms (e.g., YubiKey, Windows Hello).
- TPMAttestation: Used by devices with a Trusted Platform Module (TPM). Attestation is signed using keys from the TPM and includes a certificate chain. Used by Enterprise desktops/laptops with TPM chips (e.g., Windows machines).
- AndroidKeyAttestation: Used by Android devices with the Android Keystore. The key is generated in hardware, and attestation includes information signed by a certificate chain issued by the device manufacturer. Used by Android phones with hardware-backed keystores (TEE or StrongBox).
- AppleAttestation: Used by Apple platform authenticators, such as Touch ID and Face ID. Attestation is generated by Apple's internal APIs and includes a special certificate format. Used on Safari using Apple biometrics.
- FidoU2FAttestation: Legacy attestation format used by FIDO U2F authenticators. Returns a U2F-compatible certificate and signature. Used by older security keys (e.g., early YubiKeys) that support FIDO U2F.
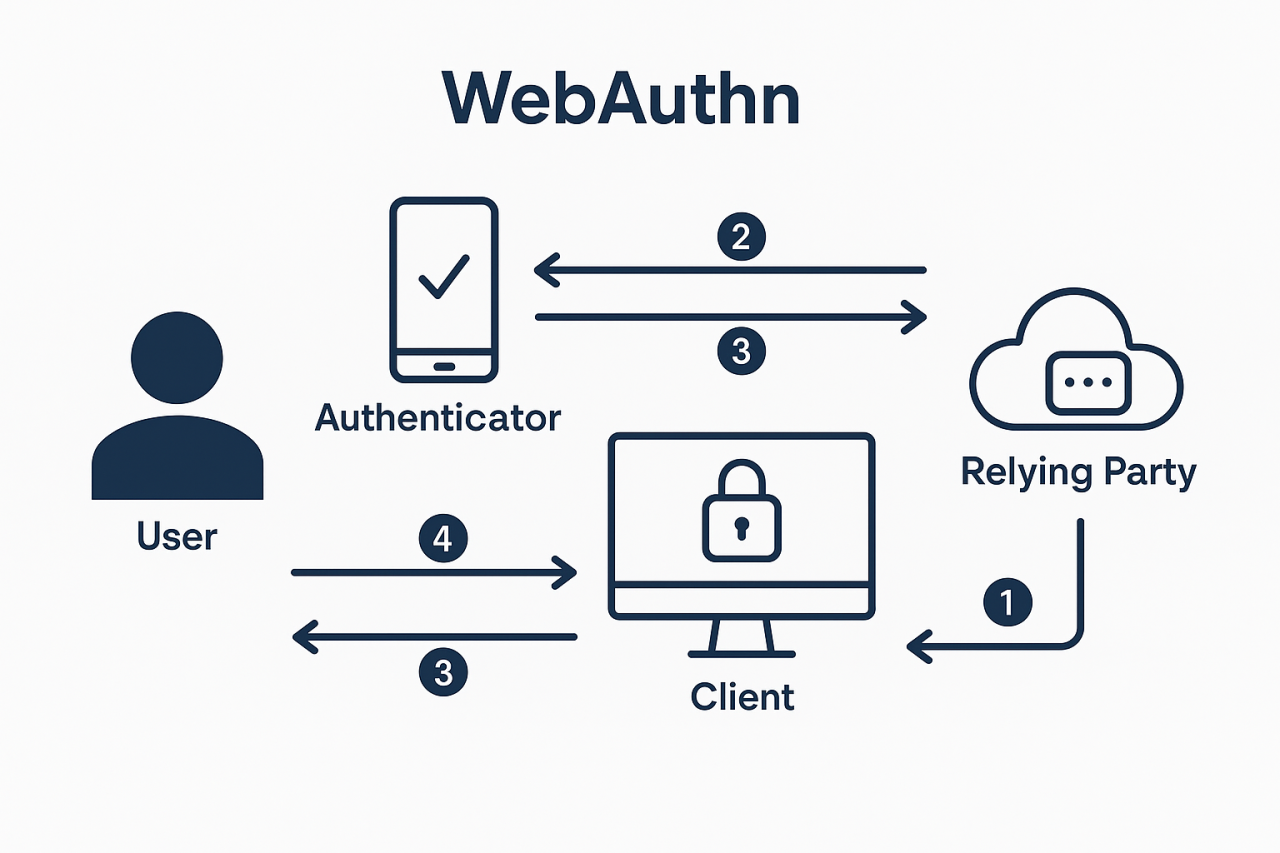
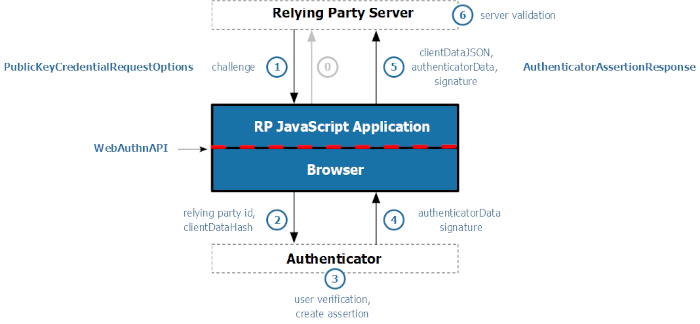
WebAuthn Flow
- WebAuthn Registration: The server generates a challenge and sends it to the client, which uses an authenticator (e.g. security key or biometric device) to create a key pair. The public key is sent back and stored by the server for future authentication.
- WebAuthn Authentication: he server sends a challenge to the client, which signs it using the previously registered private key stored in the authenticator. The signed response is verified by the server using the stored public key to confirm the user's identity.
WebAuthn Server Component
Find below a simple configuration of the WebAuthn Server:
// ... create the servers
HTTPServer := TsgcWebSocketHTTPServer.Create(nil);
WebAuthnServer := TsgcWSAPIServer_WebAuthn.Create(nil);
WebAuthnServer.Server := HTTPServer;
// ... enable for testing
WebAuthnServer.EndpointsOptions.Test.Enabled := True;
// ... WebAuthn options
WebAuthnServer.WebAuthnOptions.RelyingParty := 'localhost';
// ... bindings
Server.Port := 443;
HTTPServer.SSLOptions.Port := 443;
HTTPServer.Bindings.Clear;
With HTTPServer.Bindings.Add do
begin
Port := 443;
IP := '127.0.0.1';
end;
HTTPServer.SSLOptions.Certificate := 'sgc.pem';
HTTPServer.SSLOptions.KeyFile := 'sgc.pem';
HTTPServer.SSL := True;
// ... active
HTTPServer.Active := True;
Delphi WebAuthn Server Demo
The following Delphi WebAuthn Demo shows how to register a new credential and use after to authenticate the user.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.